
In this post we’d like to show how to expose applications via a public IP address attached to one of the nodes of a Kubernetes cluster environment in Jelastic PaaS. It can be done in two possible ways - attaching IP to Dedicated Load Balancer or to K8s Worker node.
Dedicated Load Balancer for Application Access
1. First of all, install the Kubernetes cluster from Jelastic marketplace and deploy the application. As an example, we go with Jakarta EE Cargo Tracker.
2. Click Change Environment Topology next to your Kubernetes cluster. In the opened window add a Dedicated Load Balancer node and attach a public IP address to it.
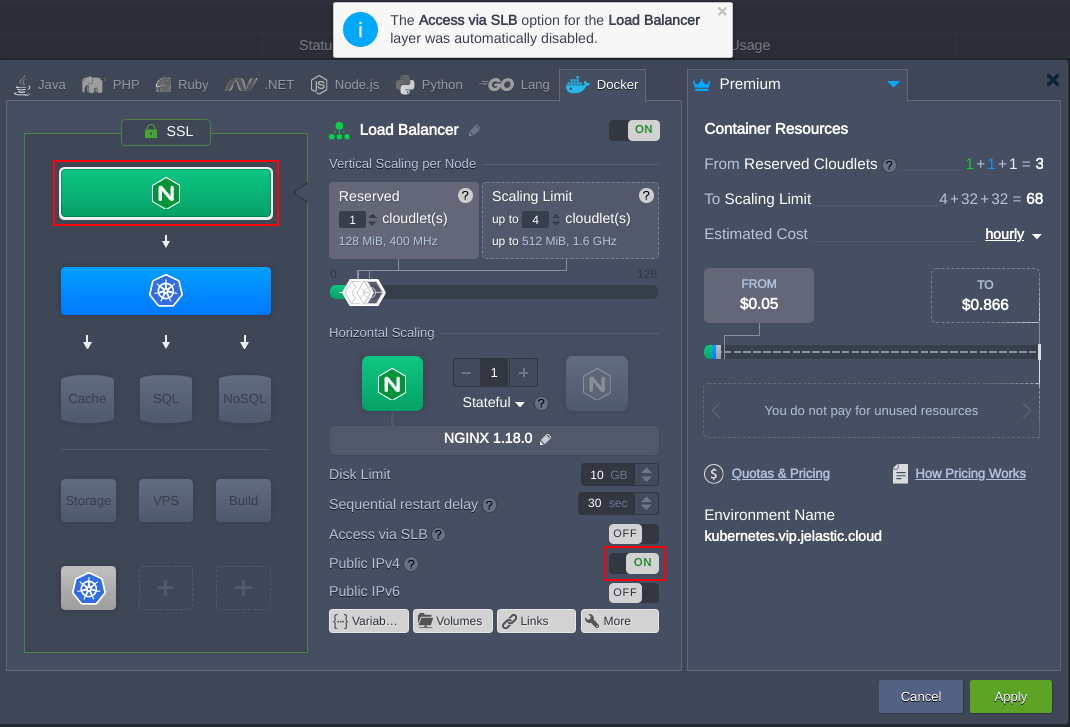
Here we use the NGINX load balancer node, but you can choose any other available (HAProxy, LS Web ADC, Varnish). Once the topology is changed it should look like as follows:
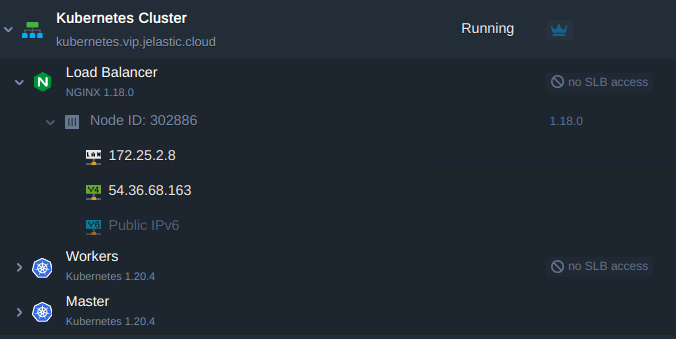
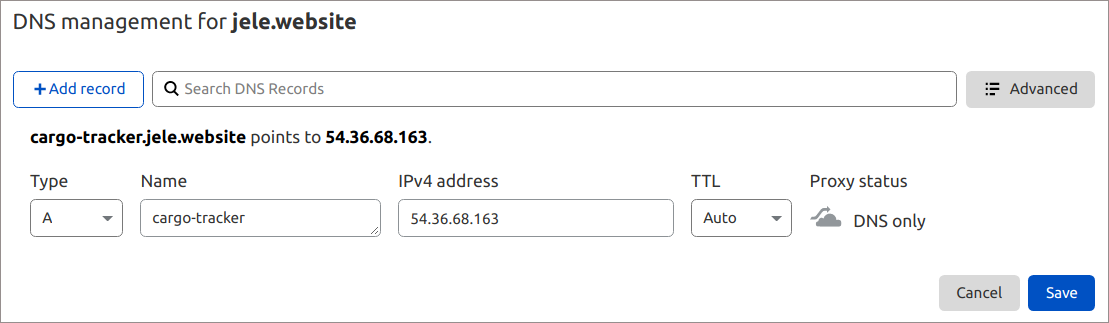
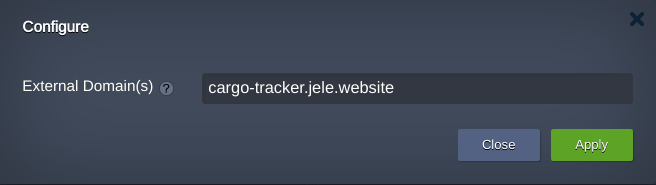
3. After that, create an A record for a custom domain using the IP address added at the previous step. For example cargo-tracker.jele.website.
4. Now you may bind the custom domain to the K8s cluster and send a request to issue a trusted Let’s Encrypt SSL certificate to secure applications’ traffic.
- Go to the load balancer Add-Ons and find Let’s Encrypt Free SSL.
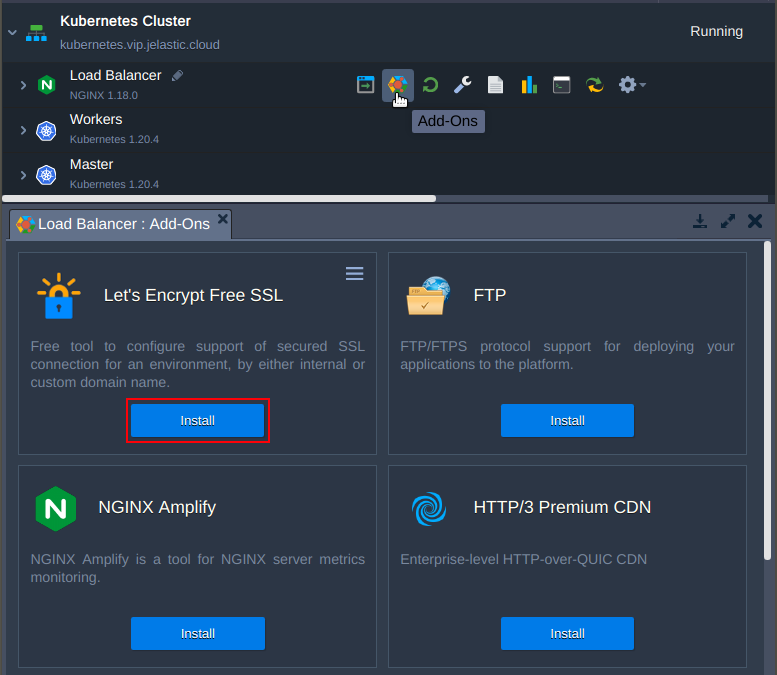
- Enter the custom domain name that we have came up with and apply it.
Now the Cargo Tracker application is available using a custom domain name https://cargo-tracker.jele.website and traffic is encrypted with the valid Let’s Encrypt SSL certificate.
Kubernetes Worker Node Public IP Address for Application Access
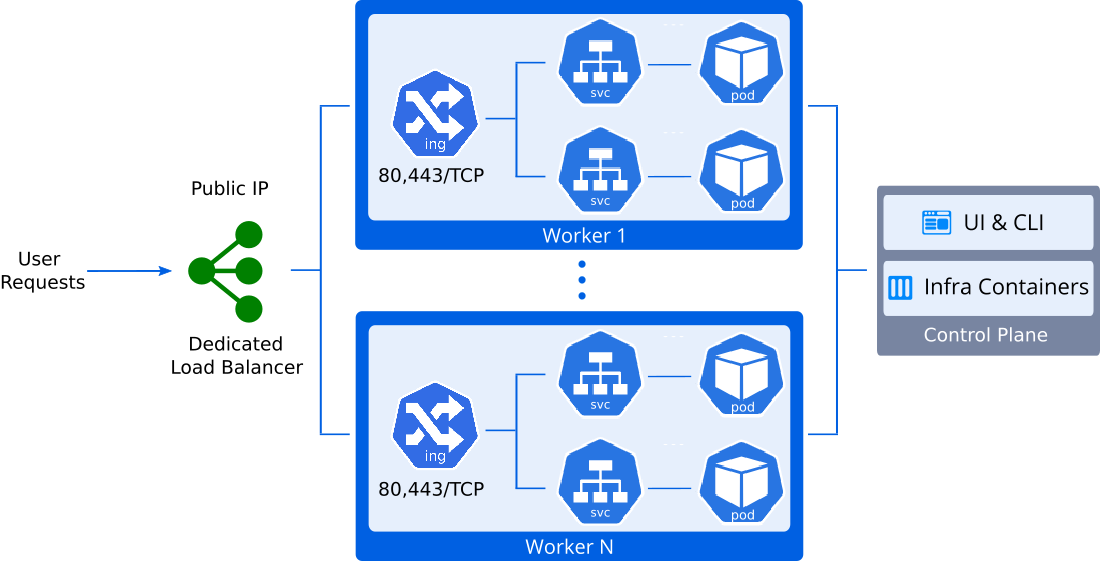
Let's take a look at another way to make application available outside of the Kubernetes cluster. The essence of this method is to make it directly accessible through a public IP address attached to one of worker nodes.
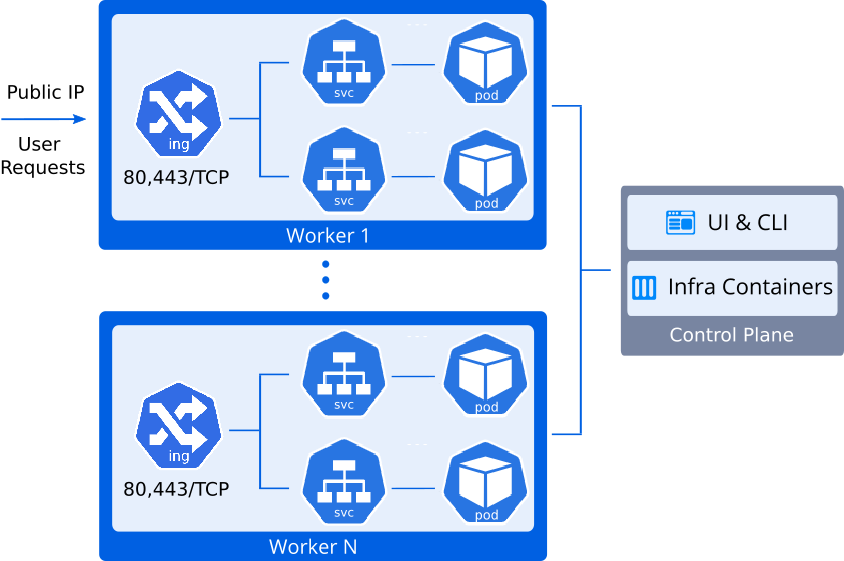
Let’s proceed on the same cluster with the Cargo Tracker application deployed.
1. Click Change Environment Topology and add the public IP address to the worker node.
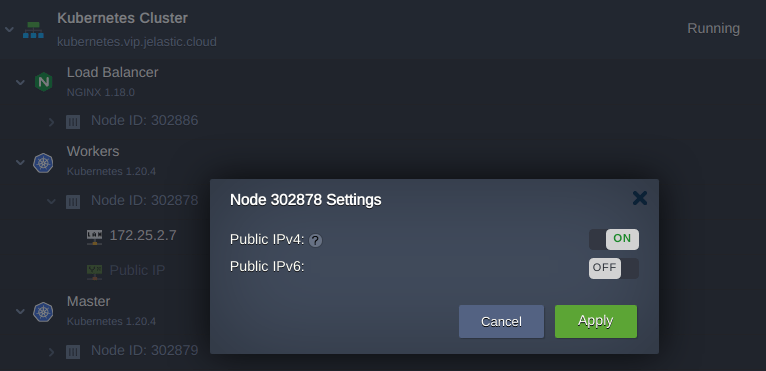
2. Create the A record for a custom domain mapping to the newly added IP address. Use a domain name different from that one used in the previous chapter. For example: cargo-tracker-worker.jele.website.
3. Then, go to the add-ons of the Control Plane node and install Certificate Manager. Along with a cert-manager controller there will be installed an NGINX ingress controller with LoadBalancer service type. It will hold the IP attached to the worker node, and will be serving the “nginx-cert” ingress class resources.
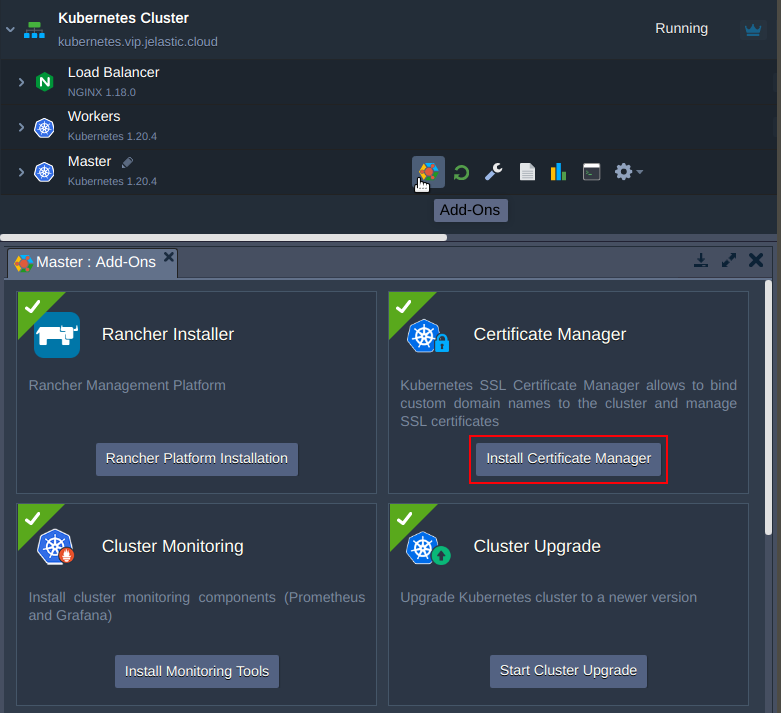
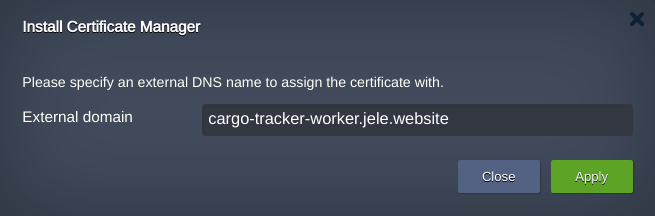
4. Enter the custom domain name and apply it.
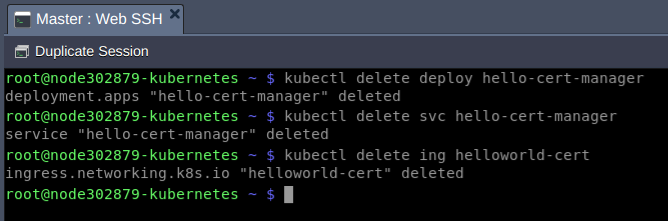
5. Upon installation, the add-on installs a test application helloworld-cert. Let’s delete the resources it takes:
$ kubectl delete deploy hello-cert-manager
$ kubectl delete svc hello-cert-manager
$ kubectl delete ing helloworld-cert
6. Finally, create an ingress resource cargo-tracker-worker that will terminate application SSL traffic and handle routing to the cargo-tracker service. For example cargo-tracker-worker-ingress.yaml:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: cargo-tracker-worker
namespace: default
annotations:
kubernetes.io/ingress.class: nginx-cert
cert-manager.io/cluster-issuer: "letsencrypt-prod"
kubernetes.io/tls-acme: "true"
nginx.ingress.kubernetes.io/affinity: "cookie"
nginx.ingress.kubernetes.io/affinity-mode: "persistent"
nginx.ingress.kubernetes.io/session-cookie-expires: "172800"
nginx.ingress.kubernetes.io/session-cookie-max-age: "172800"
spec:
tls:
- hosts:
- cargo-tracker-worker.jele.website
secretName: external-domain-tls
rules:
- host: cargo-tracker-worker.jele.website
http:
paths:
- path: /
pathType: ImplementationSpecific
backend:
service:
name: cargo-tracker
port:
number: 80$ kubectl apply -f cargo-tracker-worker-ingress.yaml
7. Upon creating the ingress, a Let's Encrypt SSL certificate will be automatically issued for this domain name with Certificate Manager. Wait for a minute and check application availability by custom domain name: https://cargo-tracker-worker.jele.website.
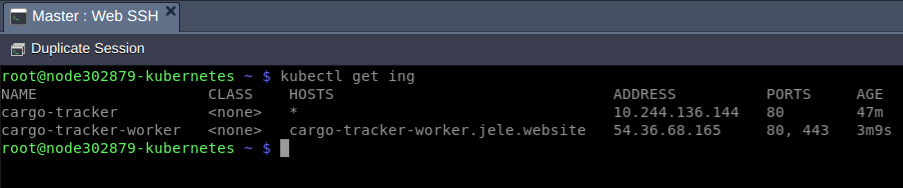
Congratulations! You’ve successfully exposed your application in two different ways and thus, you should see two ingresses:
- cargo-tracker - serves application traffic that flows via public IP address of dedicated load balancer
- cargo-tracker-worker - serves application traffic that flows directly through the public IP address that is attached to the K8s worker node
Sure, in production you need only one ingress depending on the chosen implementation. Explore easy and scalable Kubernetes hosting with Jelastic service providers worldwide.
Related Articles
Jelastic Released Kubernetes Package with Integrated Auto-Clustering and Pay-per-Use Pricing Model
Multi-Region Kubernetes Cluster Federation in Jelastic PaaS
Jakarta EE Application Deployment to Kubernetes Cluster in Jelastic PaaS