ModSecurity is an open-source, cross-platform web application firewall (WAF) module that helps to detect and prevent various attacks against web applications. The module can block common code injection attacks that ensures higher level of server security. It comes with a set of rules for cross website scripting, SQL injection, bad user agents, session hijacking, trojans, and other exploits.
Jelastic certified NGINX stacks (application servers and load balancer) are provided with the already pre-built ModSecurity module. You can follow just a few steps to enable this functionality on your containers:
1. Load the ModSecurity shared NGINX module by uncommenting the next line in the /etc/nginx/nginx.conf file:
#load_module modules/ngx_http_modsecurity_module.so;
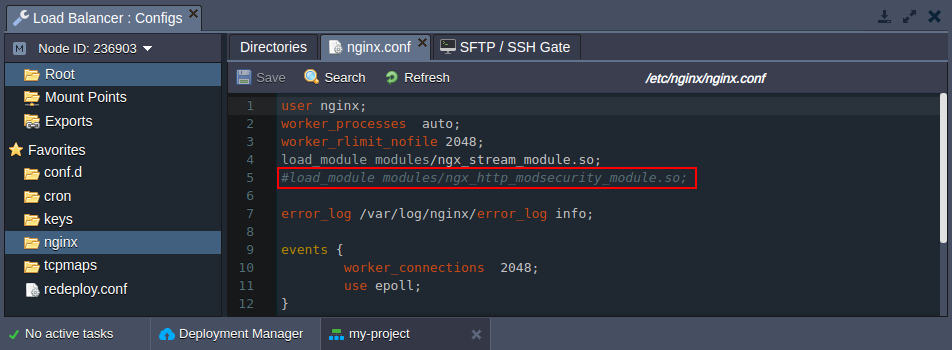
Save the changes to the file.
2. Next, enable the ModSecurity functionality by uncommenting the following lines in the same /etc/nginx/nginx.conf config for the NGINX application server stack (or /etc/nginx/nginx-jelastic.conf for the load balancer, like in our case).
#modsecurity on;
#modsecurity_rules_file /etc/nginx/conf.d/modsecurity/modsec_includes.conf;
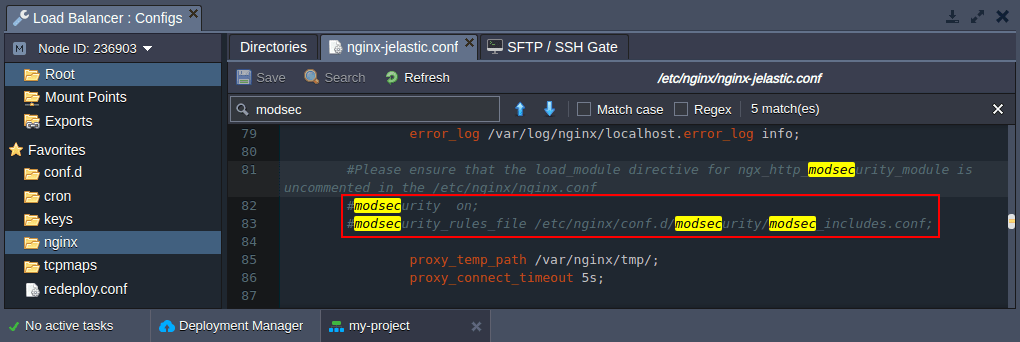
Don’t forget to Save the file after adjustments.
3. According to the /etc/nginx/conf.d/modsecurity/modsec_includes.conf config, an OWASP ModSecurity Core Rule Set (CRS) is included by default (provides generic protection from unknown vulnerabilities often found in web applications).
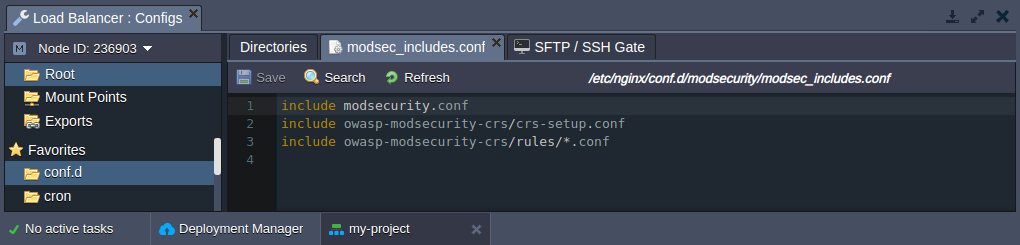
Also, if needed, you can upload your custom rules as *.conf files to the /etc/nginx/conf.d/modsecurity/owasp-modsecurity-crs/rules folder.
4. Restart the appropriate NGINX node to apply all of the performed customizations.
Now, your application is protected with ModSecurity.
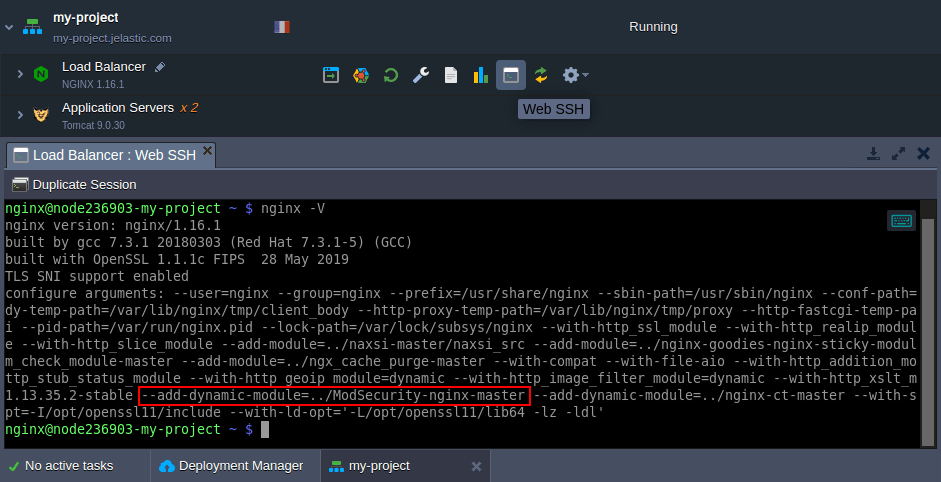
5. You can verify that it is loaded by executing the nginx -V command on the node (e.g. via Web SSH) and looking for the ModSecurity module in the list.
6. The operability of the ModSecurity can be checked by simulating an attack on your application. For example, try adding the /?q="><script>alert(1)</script> string to your environment domain. If the module works as intended, the 403 error page should be displayed, and the appropriate action logged to the error log file:
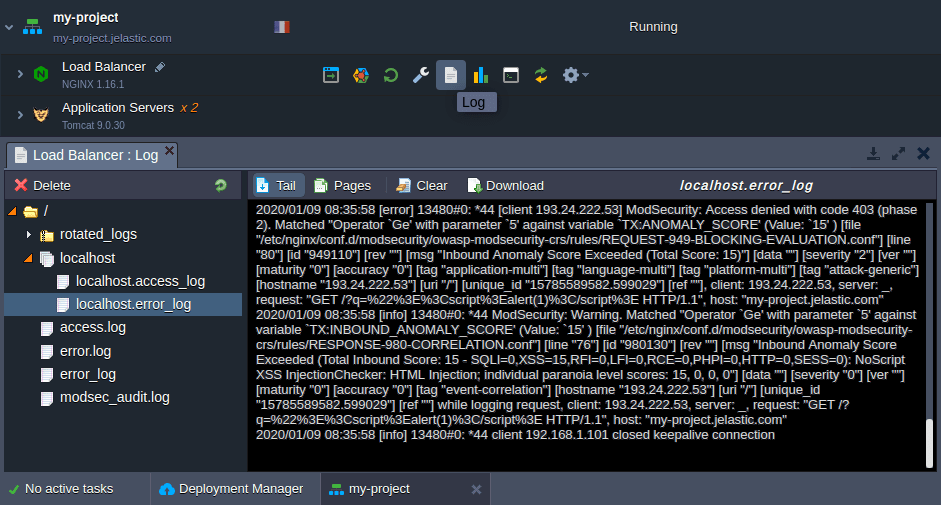
As you can see, the ModSecurity is up and working to keep your web application secure.
Start free trial and ensure high-level protection while running your projects with Jelastic Multi-Cloud PaaS.